We begin with an overview of authentication checkpoints, which are shown in the following image.
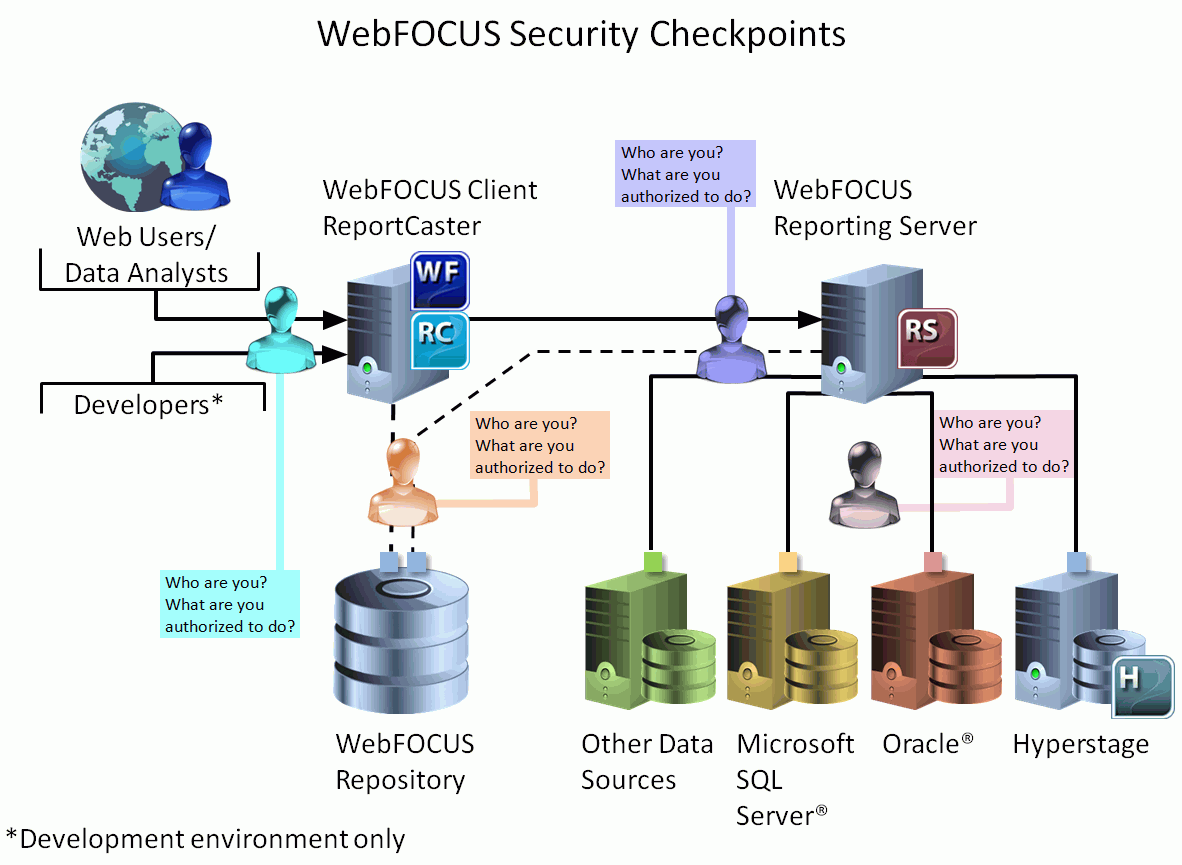
The security checkpoints serve the following purpose.
|
WebFOCUS Client |
The purpose of this security checkpoint is to ensure that only authenticated users are granted access to WebFOCUS. Then, based on their privileges they are granted access to authorized content. |
|
WebFOCUS Repository |
The purpose of this security checkpoint is to ensure that the configured database user ID has the appropriate permissions in the database to successfully execute SQL database commands required by WebFOCUS. By default, it is the database service user ID entered during the WebFOCUS installation. Credentials can be:
|
|
WebFOCUS Reporting Server |
The purpose of this security checkpoint is to ensure that authenticated users are granted access to the Reporting Server. Then, based on their user ID, or role and group, they are:
|
|
Database Servers |
The purpose of this security checkpoint is to ensure that the configured database user ID for the Data Adapters has appropriate access to connect to the back-end database servers and access data. The connecting user credentials can, in some cases, be passed to the databases to leverage data-level security, if enforced at the database level. |