How to: |
You can configure the Reporting Server to employ user-defined password encryption and decryption programs.
User-defined encryption and decryption are available from the Settings option on the Web Console Access Control navigation tree. Right-click Access Control (the top level of the tree to open the Access Control - Settings page. Set the parameter cfgfile_cipher to user defined program, which enables you to specify your password encryption and decryption programs by entering them in the cfgfile_cipher_encrypt and cfgfile_cipher_decrypt text boxes.
Note: If you choose to use password encryption outside the server, only the path to the decryption program needs to be specified.
In cases where a password is encrypted outside of the server, the encrypted password string (or label) must be used, instead of the password in server and adapter configurations. When user-defined program is chosen, all passwords for registered user in the admin.cfg file, all adapter connections in the edasprof.prf file (or user, group and role profiles), passphrases in the odin.cfg file, and pooled user passwords need to be encrypted using the same encryption program. They will be decrypted using the same decryption program. Remote Server connections in the odin.cfg file do not support the user-defined encryption option. If user-defined encryption is chosen, the Cluster Manager Feature should not be enabled.
- Select Access Control from the Web Console menu bar.
-
On the Access
Control navigation tree, right-click Access Control and
select Settings.
The Access Control - Settings page opens.
-
Select user
defined program from the cfgfile_cipher drop-down
menu, as shown in the following image.
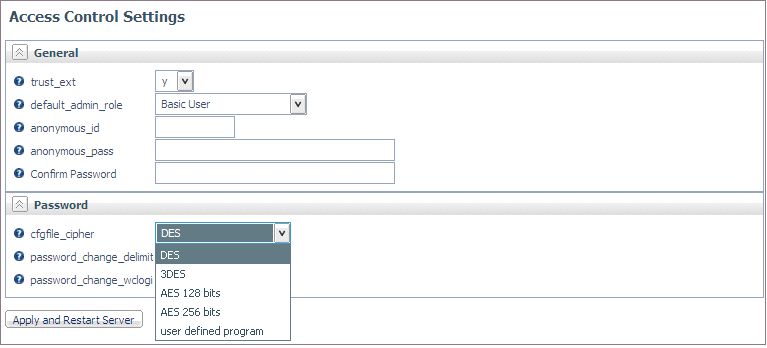
Two additional parameters are displayed.
-
Enter the
full paths to the encryption and decryption programs in the cfgfile_cipher_encrypt and cfgfile_cipher_decrypt fields
respectively, as shown in the following image.
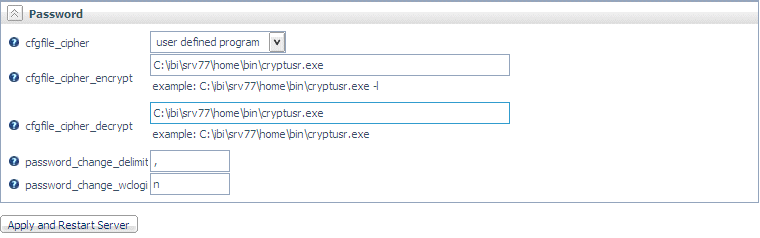
- Click Apply and Restart Server.